
Ransomware searches for vulnerabilities in your software and operating system to find a way in and carry out its malicious plans. The WannaCry ransomware discovered a security hole in the Windows operating system and used it to spread across networks.
Vulnerabilities can be found in anything, like your email client, internet browser, server, and nearly any other software that connects to the vast internet. Vendors issue patches for their software very regularly, which you should install as soon as possible, as inconvenient as it may seem. It’s better to be safe than sorry.
Want an example? Microsoft had issued a patch for the vulnerability a month before the WannaCry attack, but unfortunately, hundreds of the thousands of computers hadn’t installed it.
With an antivirus—which you should definitely have, by the way—make sure that it’s set to automatically install the latest updates.
If you’re using an outdated operating system that is no longer supported, seriously consider upgrading to a newer version as well.
As long as you’re connected to that pesky internet, there’s no such thing as absolute security. Even networks and computers that aren’t connected to the internet (air-gapped systems) aren’t absolutely secure.
An up-to-date antivirus unfortunately can’t protect you against the thousands of unknown viruses that are created every day, and a patched system won’t stop a zero-day attack (an attack that exploits a vulnerability that isn’t publicly known).
Therefore, you should try to plug the holes in your network as best you can. All major operating systems usually come with easy-to-use and pretty effective firewalls. Make sure that firewall is always turned on, and only open ports that you absolutely need.
With that being said, turn off operating system features and software that you don’t need. That includes file-sharing services and browser plugins like Flash and Java, which are rife with security holes.
Another smart measure that can reduce your attack range is keeping your work on a limited account as opposed to an administrative account. By not using an administrative account, you’ll be successfully limiting the access of the malware in the unfortunate case it does strike.
Attackers often use phishing to deliver ransomware. Phishing is a type of scam that involves targeting victims with legitimate-looking messages that contain malicious links or infected attachments. Since the targets think the email comes from a trustworthy source, they’ll download and open the attachment, which will then deliver the ransomware.
So be very careful with the emails you receive, and don’t open any attachments unless you’re absolutely certain of the source. In case there’s any doubt, use the phone or social media to verify the authenticity of the message with the sender.
You should be very wary of certain file formats, including Microsoft Office documents (.doc, .xls), executables (.exe, .bat), and compressed archives (.zip, .rar). Cybercriminals commonly use Word macros to perform ransomware attacks.
You should always be prepared for the worst coming to pass. While there have been certain scenarios where ransomware encryption has been successfully reversed at no consequence, for the most part, nothing short of paying the attackers will decrypt your files. Ain’t nobody got time for that.
That is exactly why you should always keep solid backups of your files. For files that don’t need to be modified, such as pictures and videos, you can use old-school DVDs. For other types, you can use other removable media, such as thumb drives.
External drives can work well, but they’ll be useless if they’re connected to your computer when it becomes infected. Sorry.
Cloud backups are good too as long as you make sure they aren’t mapped to local drives. Ransomware can go through all your local drives and encrypt their content, whether they’re on your hard drive or in the cloud.
Lastly, be careful when storing your archives in shared folders. Certain breeds of ransomware will scan your network and find unmapped shared folders and encrypt their content too.
We use it every day to communicate, plan our days and our projects, and transfer files and information. And with the necessity of keeping a paper trail, it’s no wonder our inboxes are overloaded by the thousands. The good news is that with careful organization and consistency, it is possible to reach “inbox zero.” Follow these seven simple steps and experience the many benefits of email bliss.
If it’s not important, delete it. The hoarding of emails is out of control, and the only way to tame it is to be honest with ourselves about which emails we need and which ones we don’t.
When it comes to emailing, labels (or filters) are your best friend. Create labels for the categories you deal with most—like expenses, project name, internal, billing, etc. By labeling each email, you’re storing it away and making it easy to find when the time comes to pull it out again.
Marketing emails are unavoidable. Companies get our information and we magically end up on an email list—but luckily they’re easy to stop. Simply find the unsubscribe link on the bottom of the email (buried in the small print) and go through the steps. If there are marketing emails you’d prefer to continue receiving, just create a label for these emails to keep them organized in one place.
Just like we create labels to store emails away, we create folders for the emails that require action. These folder names could be follow up, projects and archive. Whatever you choose, name them so you know exactly what will be needed with those particular messages—getting them out of your inbox and onto a makeshift to-do list.
If your email provider is capable, create automations for certain tasks. This could include automatically sending CCed emails to a certain folder or labeling emails containing certain keywords. This function keeps you organized while doing less of the work.
Want a virtual assistant to organize your emails for you (even from multiple accounts)? There’s an app for that. Popular applications like Boxer and Organizer help you label and organize your inbox with efficiency.
Four words: No need to reply. This phrase will keep your inbox happy and uncrowded.
With the right Chrome extensions by your side, you can do more, in less time, and with fewer hassles. But where exactly should you start? Right here.
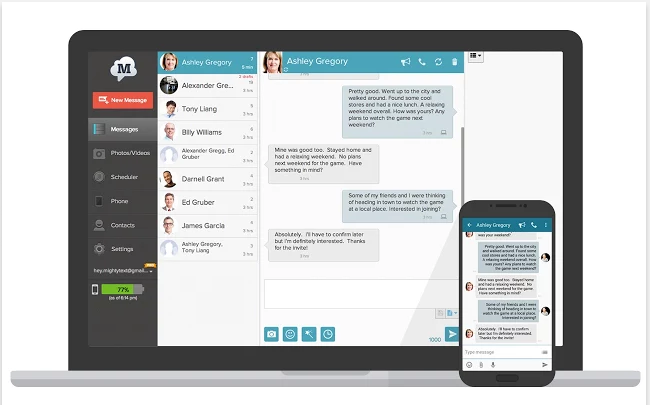
Whether it’s a work phone or a personal one, transitioning from your phone to your PC and then back to your phone again can leave you unfocused and unproductive. Avoid this with the MightyText Chrome extension. Add this extension to your browser and you can answer and respond to text messages from your computer and even receive incoming call notifications (only works with Android devices).
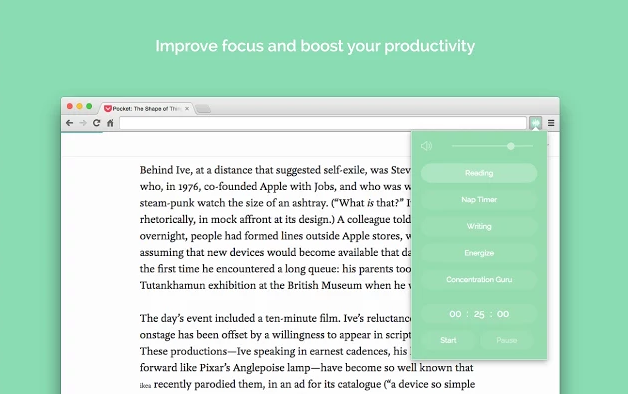
Working with no background noise or with too much of the wrong noise can make it difficult to concentrate, and Noisli gets this. Use this Chrome extension to play “cocktails of soothing ambient sounds” that can help you better focus on the task at hand. Adjust volume directly from the extension and use a complimentary task timer to plan out breaks and productivity sessions strategically.
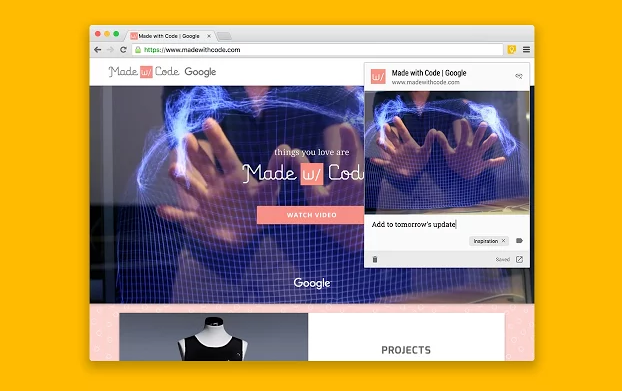
Google Keep is one of the most efficient to-do apps because it’s simple to use and easy to manage, and with its Chrome extension, things only stand to get more efficient. Add notes or to-dos to your Google Keep account by selecting the Google Keep icon in the top right corner or by right clicking with your mouse. You can add a quote, an image, or a link to the website and include a custom note to go with it.
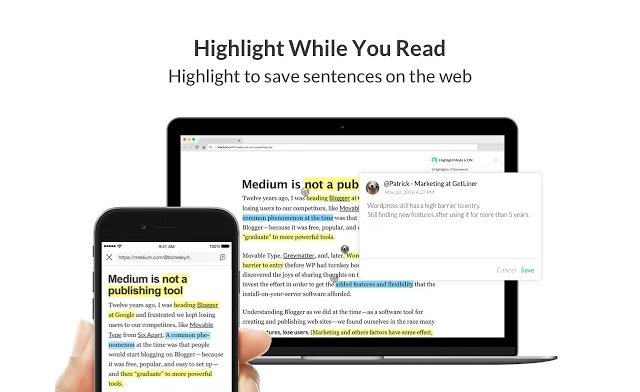
Whether you’re writing a blog for your website, tracking down content for social media, or building a report for an important project, Liner can help you keep track of the most important pieces of content. Add this extension to your browser and you can highlight online content straight from the website and even export any highlighted content to Evernote, Facebook, or Twitter.
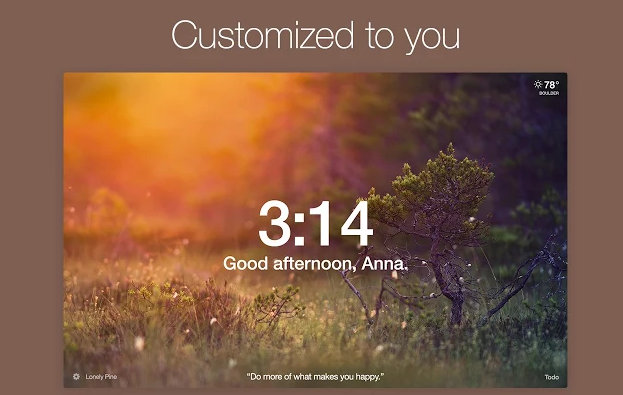
Add Momentum to your Chrome browser and you’ll be greeted with a refreshing quote and stunning image every time you open a new tab. From this screen, you can view the weather and add tasks to a custom to-do list.
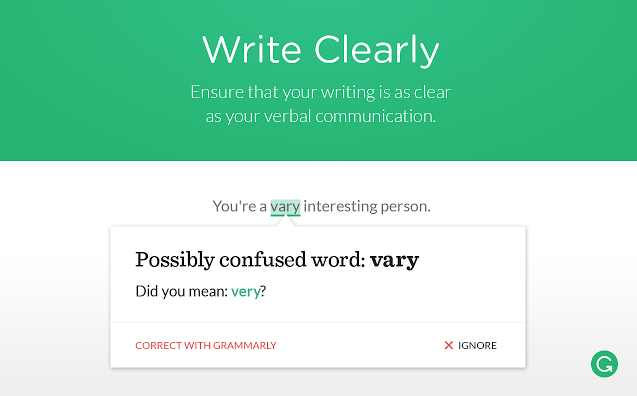
This spellchecking Chrome extension won’t just tell you what you’ve spelt wrong. It’ll also give you suggestions on how to write something better and which words would be less vague within the given context. Grammarly will explain what’s wrong and why and then give you the option to make the change or not.
Bad online habits are one thing. But bad technology habits… well, that’s a whole different story. Bad online habits can leave you swimming in malware, hackers, and leaked data – none of which is fun or pleasant. But on the other hand, bad technology habits can leave you in bodily pain, unproductive, and desperate for more time – none of which is easy to come back from. Here are a few bad tech habits to be on the lookout for.
I get it. You’re bored. You’re trying to pass the time. You simply want to see how many likes you’ve gotten on that one selfie you took in the bathroom this morning. But what is this doing for your productivity? Your focus? Your time? Nothing good, I can guarantee that. So stop. Try your best to cut back and limit the number of times you check social media during the workday. If you find this task unusually difficult, there are more than a few apps that can help you minimize all those distractions.
Some of us get a lot of emails. Like a lot. Like too much for one person to handle. But whether you check these emails now, five minutes from now, or an hour from now will typically not make a difference in the grand scheme of things. So do yourself a favor and hold off. Set aside 15-20 minutes every hour or so. If you can pull it off, shoot for 15 minutes every two hours. This should help you maintain focus for longer.
Do you ever find yourself sitting way too close to the computer screen? And usually you realize this when someone walks up behind you and asks if you need glasses. But then you turn around and you’re already wearing glasses. Don’t do this. Your face should be anywhere from two to three feet away from the computer screen. Sit any closer and it could damage your eyesight and land you in a world of headaches and strained eyes.
Sure, your eyes should be at least two feet away from your computer screen… but that’s not the only thing you should keep in mind. You also need to remember to rest your eyes every so often. The rule of thumb here is 20-20-20 – every 20 minutes look at something 20 feet away for 20 seconds. This can help relieve some of that strain your eyes can feel staring at a computer screen all day.
It’s 10:30 at night and you’re fading. But for some reason, that phone is still in your hand and you’re still swiping through Instagram, tweeting up a storm, or lost somewhere inside YouTube… which is no good. You see, those bright lights have been known to make it harder for people to fall asleep at night because the light messes with your melatonin levels and disrupts your sleep cycle. Therefore, if it is late at night and if you are still on your phone, then keep your screen dimly lit and if possible, switched to a warmer spectrum of color. If you have an iPhone this is simple. Just visit your Settings or swipe up from the home screen and tap on Night Shift. You can manually turn the feature on or off, or you can schedule night shift to turn on and off at a specific time every day.
Everyone these days is throwin’ out tech terms, using them in normal conversation like it’s nothing. But do any of these people – or you, for that matter – actually know what these terms mean? If not, here’s a quick list of 8 commonly used tech terms to get your mind prepped.
A web app is a website that looks and feels like an app. You can access a web app from your browser just like any other website. But unlike traditional websites, a web app allows you to access other components of the site without reloading it. An example of a web app could be Buffer, Dropbox, or the web version of the Microsoft productivity suite.
There’s the backend of a website or app and then there’s the frontend. The frontend is everything a user sees and interacts with, like the fonts, colors, menus, and buttons. Some people like to say that the frontend is what makes the website or app look ‘pretty.’
It’s important not to think of your keyword as one word. Your keyword can be as long or as short as you need it to be. This word or set of words should encompass the main idea of your webpage and should be incorporated within your Meta Description. Typically, the longer the keyword is, the more specific it is.
Any malicious software meaning to do harm to your computer or other connected devices is considered malware. This includes viruses, adware, trojans, and worms.
When you start getting into very specific keywords, they become long tail keywords. This type of keyword is usually applied to blog posts or other content-heavy material. An example would be going from “potty training animals” to “potty training a small dog in an apartment.”
IT stands for information technology, and it refers to all the hardware and devices within your business that sends, stores, and receives data.
An MSP stands for managed service provider, and it is a company who fully manages another company’s technology. Within this MSP, there are a handful of technicians who provide their clients with preventative hardware maintenance and routine network monitoring. The goal is to prevent IT issues from occurring and avoid downtime.
All the content you push online – through social media, vlogging, blogging, cornerstone pieces, and the likes – is considered content marketing. It builds up your brand, focuses on key areas, and can help your business attract new leads and maintain the attention of current consumers.

