
Have you ever used a public Wi-Fi signal here in Bakersfield? If you live here, it’s highly likely and it’s even more likely you’ve tapped into a free signal during your travels. We are a culture on the move and we are becoming more and more mobile every day. Whether you’re at a coffee shop, 32,000 feet in the air over the Pacific Ocean or even simply within some cities jurisdictions, you have Wi Fi options to tap into. As of 2017, there were 9 billion mobile devices in use globally and over 300 million Wi-Fi hotspots with an anticipated 432.5 million hotspots by 2020. Wi-Fi is such an integrated part of society, it even has an official day of recognition each year – June 20th.
With the availability of public Wi-Fi, more than 43% of all workers in the United States were able to take advantage of working remotely from their office and while some may have their own private Wi-Fi hotspots, many rely on the public access.
With all of the positive benefits a connected society has, there leaves as much opportunity for criminals to exploit the system. Public hotspots leave a very open avenue into your digital fingerprint. Bank accounts, credit card numbers, passwords, and so much more. In 2017, there were over 143 million hacks reported in the United States alone from Wi-Fi entries.
Here are some of our biggest threats when it comes to using these hotspots:
This is one of the easier attacks and can be the beginning of a very damaging effort. On public Wi-Fi, tools such as packet analyzers and LAN keylogger software can give someone sitting nearby everything they need to act as you or your employee. In some cases the software can monitor the screen activity of each computer on the network. All of this unknown to the victim
Thanks to software vulnerabilities, malicious code can be injected into any device on the network. This opens up a world of opportunity for a hacker. Malware can be used to continuously feed information to someone outside your organization. The malware can also be used to activate the microphones on laptops and mobile devices for eavesdropping. The installation of malware is the most dangerous risk. This is because your employee could have compromised your network a long time ago and you wouldn’t know because they access from various locations all the time. So any behavior may not be immediately detectable while using their credentials. The depth of compromise is entirely dependent on the creativity of the hacker.
These are common especially for people who do not visit sites with https. A man-in-the-middle attack occurs when a hacker interceptions your communications. So before you data reaches its intended audience, it goes through the hacker first. This can also apply to passwords and usernames. The man-in-the-middle method is commonly used for eavesdropping and intercepting file or financial transfers.
Encryption means that the information that is sent between your computer and the wireless router are in the form of a “secret code,” so that it cannot be read by anyone who doesn’t have the key to decipher the code. Most routers are shipped from the factory with encryption turned off by default, and it must be turned on when the network is set up. If an IT professional sets up the network, then chances are good that encryption has been enabled. However, there is no surefire way to tell if this has happened.
With the vulnerability public Wi-Fi leaves us open to, how can anyone consider tapping into it? The good news is that all hotspots are NOT created equally and there are a lot of things you can do to protect yourself.
ALWAYS confirm the network name. Bumming Wi-Fi at a local coffee shop? Looking for a network in a hotel lobby? Wherever you are, never assume you know the network name. Some hackers create free Wi-Fi spots that don’t require passwords, making it easy to access your information due to lack of encryption security. To be sure, verify with an employee or triple check the spelling if it’s printed out before connecting.
Use HTTPS when browsing the web. Hypertext Transfer Protocol Secure is the secure version of the HTTP you usually use when visiting a URL. Adding that simple ‘S’ at the end encrypts everything between your browser and the sites you visit, keeping information like banking passwords and credit card numbers safe and sound.
Use encrypted storage security. Storing your important files in encrypted storage means they’re password protected and as safe as the money in a bank vault. You can find a range of encryption options, from free downloads to software for purchase that offers more security features. This will ensure that even if hackers do gain access to your computer via an open network, they will not be able to enter your protected vault of files. Think of it like a locked treasure chest within your system, and you’re the only one with the map and the key.
A VPN (Virtual Private Network) is simply a group of networks that secure and encrypt communication, and can be connected to remotely. Businesses use this often to connect individuals to network resources, but you can use it to secure your public Internet connection and to protect any data you’re sending and receiving. However you choose to use your VPN, make sure you choose a service that offers protocols on connectivity, server location, and offers features that meet your needs.
Make a turn-off checklist and follow it. When you’re planning to visit a location where you know you’ll be using a public network, turn off automatic connection to Wi-Fi on your device. This guarantees you’ll never accidentally join a fake network created to steal your data. Also remember to turn off Wi-Fi when you’re done browsing, always ensuring that you are in control of what, when, and how you connect.
Finally, make it a habit to turn off sharing. You never know who’s roaming around trying to covertly access your information. If you have sharing enabled on your device and forget to turn it off, you’re basically waving a flag to potential cybercriminals and saying, here’s an easy target! And never, ever save passwords. It’s convenient but it makes it even easier for any potential threats to access your electronic information.
It’s simple. Make sure that your passwords are strong and unique. Don’t use your birth date, phone number, social security number, family members name or your pet’s name – these can be easily guessed by a cyber crook usually just by looking over your social profiles.
Don’t use your birth date, phone number, social security number, family members name or your pet’s name – these can be easily guessed by a cyber crook usually just by looking over your social profiles.
It’s also important that you don’t reuse passwords between your accounts or change them too often. A good password should last a year. Although this may sound counter-intuitive, frequent updates to passwords often result in “password1”, “password2” patterns and these are easy to uncover.
Unfortunately, it’s not uncommon in our current culture to face major security breaches on our favorite platforms, such as the recent ones that involved LinkedIn, MySpace and Tumblr, where hundreds of accounts details went for sale on the dark web. Think about it. If you used the same pass everywhere, attackers would be able to quickly access all of your other accounts quickly (and they know it).
The bottom-line is that breaches are on the rise year over year and according to Netherlands-based security firm Gemalto, more than 2.6 billion records were breached in 2017, which breaks down to:
To put that in perspective, there were “only” 1.6 billion records lost or stolen in 2016 — in other words, there’s been a 163% increase in breached records. These numbers could be even higher, but nearly 60% of the total breaches include an unknown or unreported number of compromised records (similar to the Yahoo breach, which was reported as a larger breach over time – now listed at 3 billion-plus records).
Prioritizing breach-prevention tools and policies is extremely critical for small businesses. Hackers know small businesses have less resources to counter their efforts (whether it be shortage of staff or budget), and have targeted them at an alarming and increasing rate each year, according to Symantec’s Internet Security Threat Report.
What’s more alarming than that? Almost 90% of small business owners don’t feel like they’re at risk of experiencing a breach.
According to Statista.com, 22% of respondents stated that they used different passwords for every online login.
Password management company Keeper Security released a list of the most common passwords of 2017 and the most common password, making up nearly 17% of the 10 million passwords the company analyzed, was “123456.”
See their reported top 25 passwords below:
After you determine your password for various platforms, avoid writing them down at all costs. This includes creating an Excel spreadsheet or an office document for your team to share.
Instead, start using a password manager, such as LastPass. It will remember all of your passwords and store them in a secure way. This way, you’ll only have to remember one master password, the one for your main LastPass account.
In addition, avoid using the “REMEMBER PASSWORD” option on websites. With the convenience of being remembered by your favorite platforms comes the ability for crooks to effortlessly cruise right into your cyber world.
When it comes to creating your passwords, consider these best practices:
This rule helps you to build passwords that are strong as steel. Use eight characters with one upper and one lower case, a special character like as asterisk and a number. The more random the better.
Here’s another hint for an effective password policy to foil hackers. Make sure the numbers and symbols are spread out through the password. Bunching them up makes the password easier to hack.
Everyone involved in a small business needs to understand there’s a big difference between security and convenience when it comes to passwords. It needs to be clear using personal information like your first name and birth date is a recipe for disaster. If a hacker ever gets his hands on company HR data, this information will be the first set of combinations he tries.
It might sound safe to go to the dictionary for a password, but hackers actually have programs that search through tens of thousands of these words. Dictionary attack programs have been around for years.
The average person can only remember 10 characters or less. Long passwords run the risk of being written down so they can be remembered.
Abbreviations are usually immune to dictionary attacks. So TSWCOT for The Sun will Come Out Tomorrow is a good choice for a secure password. Remember to add symbols and numbers.
Don’t use these as a shortcut to identifying your department or who you are. It might be temping for an accountant to use CPA. However, that opens a cybersecurity door wide enough for a hacker to walk right through.
Don’t become a statistic this year and help keep your employees safe as well.
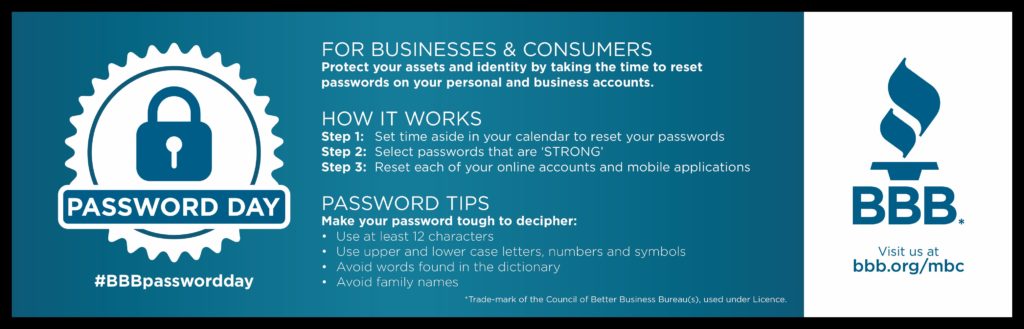
Celebrate World Password Day by visiting PasswordDay.org and taking the World Password Day pledge, sharing a password tip on social media, changing an old password to a long, strong one or by turning on two-factor authentication for your important accounts.
Security researcher Mark Burnett first encouraged people to have a “password day,” where they update important passwords in his 2005 book Perfect Passwords. Inspired by his idea, Intel Security took the initiative to declare the first Thursday in May World Password Day in May 2013. Submitted by Big Monocle in 2016, Password Day is meant to create awareness of the need for good password security.
———————————————————————————–
Founded in 2012, Big Monocle designs creative branding and marketing that tells impactful stories. Their growing, energetic team of talented professionals focus on developing experiences and connecting with every client.
You’ve probably heard by now that over 50 million Facebook users’ private information had been stolen by Cambridge Analytica during the 2016 presidential campaign. Here’s a summary of the story:
Since the exposure of this story, users around the world have been anxious to learn what information a data beast like Cambridge Analytica could have accessed after accessing the social platform giant.
I’m here to report that Facebook has an incredible memory and downloading my own Facebook data was not only a walk down memory lane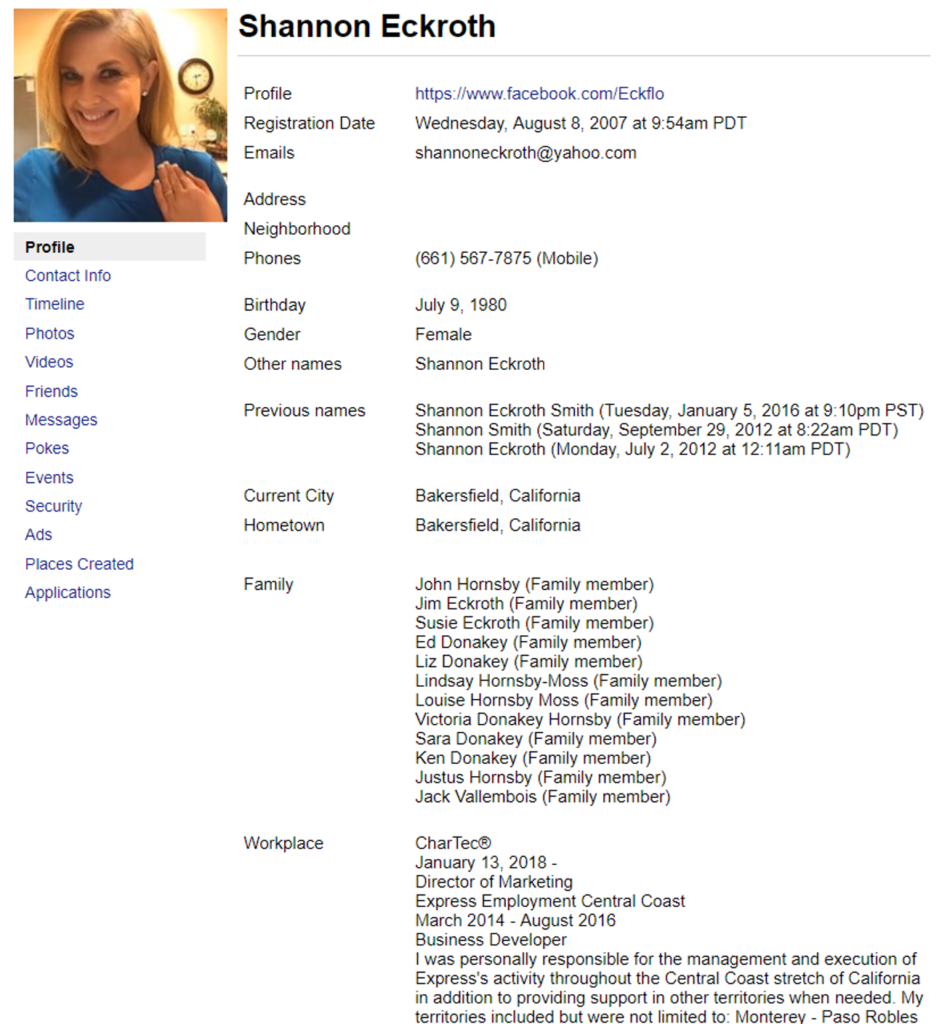 but also terrifying. I have been a member of the site since 2007 and was presented with an insane amount of personal details that have been collected on my behalf over the last 11 years.
but also terrifying. I have been a member of the site since 2007 and was presented with an insane amount of personal details that have been collected on my behalf over the last 11 years.
As you can see, it not only leaves space for contact information but my family is detailed along with an extensive work history to which is actually saved “privately” on my profile. Apparently “private” only meant that third parties and hackers could see it, not the general public.
In addition, phone numbers and email addresses of over 20,000 people I had come across in my 10 years of sales and recruiting had been stored, many of which belong to people not even on Facebook. This was all listed under the “Contact Info” and obviously scraped from my mobile devices.
Under the “Friends” tab, I was able to see a running tab of who I had connected with over the years, when I connected and when I disconnected as well! With an account constantly flexing around 5,000 friends, the list in its totality under this tab included over 7,400 people.
The “Messages” tab was also surprising. If “de-friending” someone wasn’t enough to remove them from my data archive “Friends” tab, it certainly wasn’t enough to remove the messages either. Every conversation that I had encountered over the last 11 years from friends, strangers, exes and otherwise all reappeared and were obviously accessible to third parties and hackers.
But still, it gets crazier!!
When it came to the companies targeting me based on my preferences under the “Ads” tab, I was really surprised to find so many brands that I had never directly reached out to. After a little online research, I found this article by the Washington Post that outlines 98 touch points Facebook uses to connect us to their paid advertisers. It’s important to note as well, one of my male colleagues had a few surprising advertisers collecting his data: Rod Stewart, Sally Beauty and Cyndi Lauper. (He said he’s not a fan of any of those brands.)
There were over 1000 companies in this list for me.
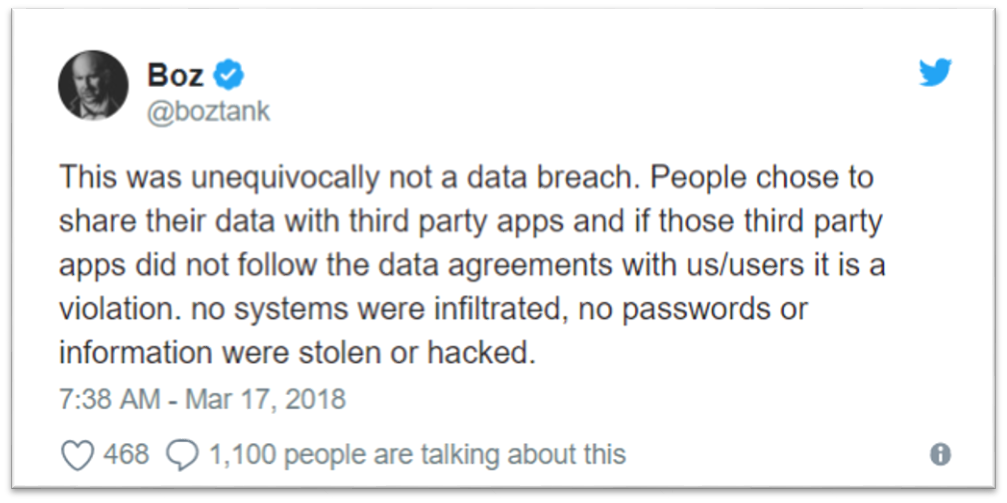 But Facebook doesn’t consider this exposure a hack or even a “data breach”. They will go as far as accepting that this was a “breach of trust” but that’s where their ownership stops.
But Facebook doesn’t consider this exposure a hack or even a “data breach”. They will go as far as accepting that this was a “breach of trust” but that’s where their ownership stops.
Deputy general counsel Paul Grewal released a statement on Saturday writing that “the claim that this is a data breach is completely false” because the researcher got consent from everyone involved. Andrew “Boz” Bosworth, Facebook’s former vice president of ads, took a similar stance.
So many of us are left asking, “Is it time to delete our Facebook accounts?”. Some brands went noticeably offline this weekend, deleting their Facebook pages, even igniting a #deletefacebook movement, but is it necessary?
Not really. There are plenty of ways we can start protecting our privacy more than ever. Check out this article for some easy “Spring-Cleaning” tips to a safer online experience.
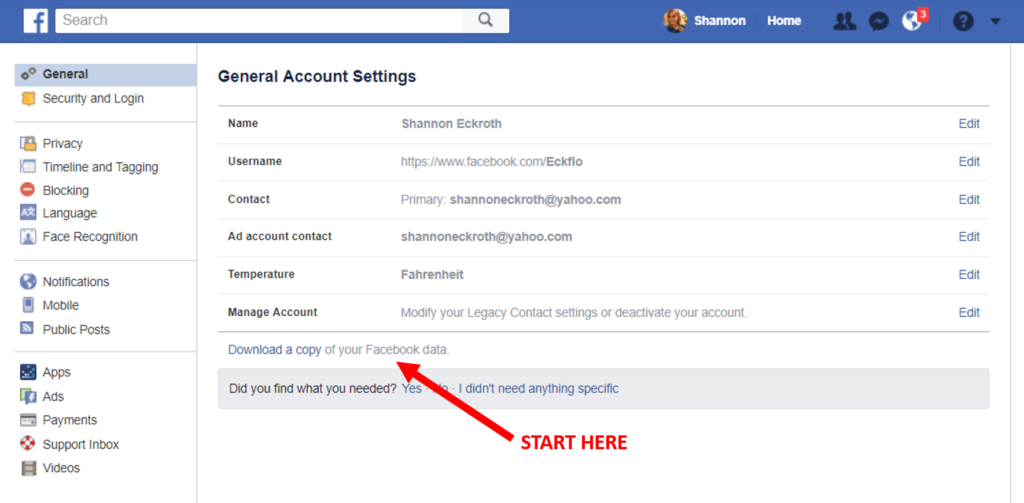
If you would like to download your own data, (and I think you should) follow the simple steps offered in your Facebook Privacy Settings:
On Monday, February 12th, TheHackerNews reported that the Pyeongchang Winter Olympics taking place in South Korea was disrupted following a malware attack before and during the opening ceremony on Friday. Travis Day of ARRC Technology stated in response to the attack, “It is a DDoS (distributed denial of service) and is common for large scale events like the Olympics. The new threat on the rise is cryptojacking and its replacing ransomware on the threat landscape as explained in a recent article with Wired.com.”
The cyber attack coincided with 12 hours of downtime on the official website for the Winter Games, the collapse of Wi-Fi in the Pyeongchang Olympic stadium and the failure of televisions and internet at the main press center, leaving attendees unable to print their tickets for events or get venue information.
The Pyeongchang Winter Olympics organizing committee confirmed Sunday that a cyber attack hit its network helping run the event during the opening ceremony, which was fully restored on 8 am local time on Saturday—that’s full 12 hours after the attack began.
Multiple cybersecurity firms published reports on Monday, suggesting that the cause of the disruption was “destructive” wiper malware that had been spread throughout the Winter Games’ official network using stolen credentials.
Dubbed “Olympic Destroyer” by the researchers at Cisco Talos, the wiper malware majorly focuses on taking down networks and systems and wiping data, rather than stealing information.
The Talos researchers would not comment on attribution, but various security experts have already started attributing the Olympic Destroyer malware to hackers linked to either North Korea, China or Russia.
According to the analysis by Cisco Talos, the attacker had intimate knowledge of the Pyeongchang 2018 network’s systems and knew a “lot of technical details of the Olympic Game infrastructure such as username, domain name, server name, and obviously password.”
“The other factor to consider here is that by using the hard-coded credentials within this malware it’s also possible the Olympic infrastructure was already compromised previously to allow the exfiltration of these credentials,” researchers said.
The Olympic Destroyer malware drops two credential stealers, a browser credential stealer and a system stealer, to obtain required credentials and then spreads to other systems as well using PsExec and Windows Management Instrumentation (WMI), two legitimate Windows administration tools used by network admins to access and carry out actions on other PCs on a network.
The researchers noted that both built-in tools were also abused by the Bad Rabbit ransomware and NotPetya wiper malware last year.
Once installed, the malware then first deletes all possible “shadow” copies of files and Windows backup catalogs, turn off recovery mode and then deletes system logs to cover its tracks and making file recovery difficult.
“Wiping all available methods of recovery shows this attacker had no intention of leaving the machine useable. The sole purpose of this malware is to perform destruction of the host and leave the computer system offline,” reads the Talos blog post.
It’s difficult to accurately attribute this cyber attack to a specific group or nation-state hackers due to sparse of technical evidence to support such a conclusion as well as hackers often employing techniques to obfuscate their operations.
RELATED ARTICLES:

